COMP6210 – Ethical Hacking and Penetration Testing Final Project
Disclaimer: All blog posts that are related to ethical hacking are used for educational purposes only.
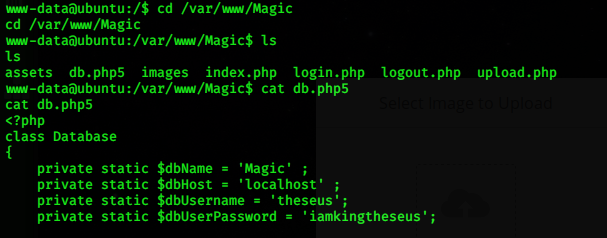
Database Content Disclosure
as for this step after executing remote shell access, I started to find the vulnerabilities by searching all sensitive data on the server’s databases in here I use MySQL dump to explore all the sensitive data inside the database
No Comments »
RSS feed for comments on this post. TrackBack URL