COMP6210 – Ethical Hacking and Penetration Testing Final Project
Disclaimer: All blog posts that are related to ethical hacking are used for educational purposes only.
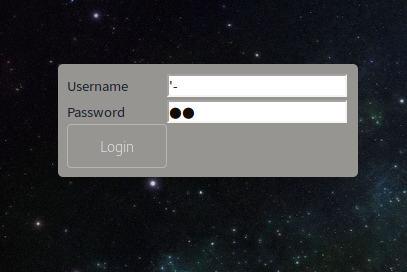
SQL Injection
After finding out that the target has a web application then I decided to open the IP address on the web browser. after opening the web page is open the next thing that I did is to log in the way that I did is to type with the same SQL query on username and the passwords until I reach to the next page
No Comments »
RSS feed for comments on this post. TrackBack URL